




Since the innocent child knowing and approaching a magical box named “Computer”, his life had a big change.
After years of experiences and explorations in IT related fields – IT Executive, Customer Support Executive, IT Consultant, Programmer, System Analyst, Data Migration Specialist, IT Specialist, and IT Manager.
The child believes in the Information Technology related businesses, especially the IT Solutions, IT Infrastructure, Data Management, Data Backup and Recovery (Risk Management) and etc. still have room to inject with more complete, flexible, and customizable elements. These elements are extremely useful and required by our business nature without self-realize, and always been ignored.
In few years lately, no matter how advanced and how much improvement technology had been moving forwards, the growing guy aware that the IT Consultancy and Services is a MUST to maintain the infrastructure, all machines, its relevant systems, security, networking, and etc.
This continuous maintenance is deeply required just like our air-con required periodic services, human body required seasonal recharges, etc. Without continuously maintenance, the businesses may not go as far as it supposes to, and as smooth as it should be.
Our world getting advanced and relying on internet. Internet is one of the most important elements on our daily life nowadays. Emails, Social Apps, Cloud Storages, Remote Connections, Driverless Automobiles, and etc. are fully rely on internet.
Internet is open to public generally, although it can be improved by multi-factors authentication, encryption-decryption, firewall, internet security, Anti-Virus, and etc., but its security will be questionable.
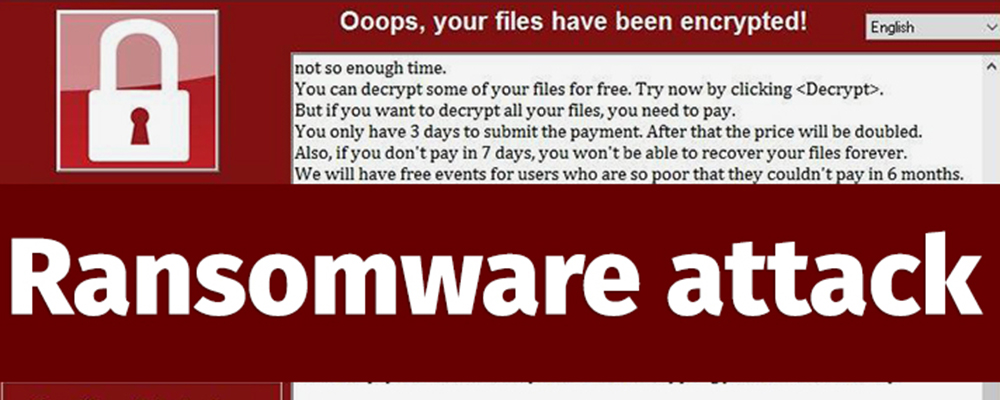
However, no matter how strong and powerful is the security, there always no 100% guaranteed, and still have chances for threats attacks, ransomware attacks and other invasions, it only matters of difficulty levels and time consumed.
Ransomware attacks news are getting weekly nowadays and increasing, which hackers are attacking almost everything through every possible channel, such as Emails, Social Apps, Remote Desktop Connection, Network Attached Storages, and etc.
We believe and we know the most common and easy method to avoid that risk will be data backup, the more backup copy of our important data, the better and safer we are.
We can do backup on premises, external storages, virtual images, and cloud.
“ techhouz ” (House of Technology) was established on 2010.
We carrying a philosophy, “ we Search, we Analyse, we Provide. ”.
We holding a principle, “ Our Customers + Our Partners = Us ”.
“ we Search ”
Whenever our customers’ and our partners’ lives or businesses, there is a need on Information Technology assistant.
“ techhouz ” will assist our customers and our partners, by searching, and presenting the market available plans and solutions.
“ we Analyse ”
When we have the suitable and accurate plans and solutions, we will start to do necessary analysis by factor in our customers’ and our partners’ terms and conditions, budget, business environment and etc. to choose most suitable solutions for our customers and our partners from time to time.
“ we Provide ”
We will provide our customers and our partners, only the agreeable and suitable solutions in multiple phases. We won’t just stop our services after the installation and implementation of the solutions, we will provide relevant training, and provide continuously support and maintenance. Whenever there is a need, we will provide the solutions update or solutions upgrade, and advise our customers and our partners from time to time based on the technology trends.
We serve our customers and our partners as a family; we will do business and grow together as a family.
Let's “ techhouz ” run your IT Department, while you running your businesses.
Let's “ techhouz ” manage your Data Backup and Recovery, while you selling your products and services.
Let's “ techhouz ” assist you to transform your available data into meaningful and presentable information, while you closing your sales.
 director
director
 " t e c h h o u z " are capable to assist in your business as your IT Executive, IT Engineer, System Administrator, Database Administrator, System Architect, Risk Management Manager and etc.
" t e c h h o u z " are capable to assist in your business as your IT Executive, IT Engineer, System Administrator, Database Administrator, System Architect, Risk Management Manager and etc.
 " t e c h h o u z " clearly defined out role, visualize the success and be oriented towards the results.
" t e c h h o u z " clearly defined out role, visualize the success and be oriented towards the results.
 " t e c h h o u z " do provide IT Infrastructures Setup, Troubleshoot and Administration.
" t e c h h o u z " do provide IT Infrastructures Setup, Troubleshoot and Administration.
 " t e c h h o u z " do assist in IT Procurement, such as Server, Workstation, Notebook, Software, AntiVirus, Software Licensing Auditing and Monitoring, and etc.
" t e c h h o u z " do assist in IT Procurement, such as Server, Workstation, Notebook, Software, AntiVirus, Software Licensing Auditing and Monitoring, and etc.
 " t e c h h o u z " do consult, install, configure, troubleshoot, setup, administrate, and maintain our customers' office networking.
" t e c h h o u z " do consult, install, configure, troubleshoot, setup, administrate, and maintain our customers' office networking.
 " t e c h h o u z " do listen to customers' requirements, study the needs, consult and advise, planning, deploy and maintain the software in full cycle.
" t e c h h o u z " do listen to customers' requirements, study the needs, consult and advise, planning, deploy and maintain the software in full cycle.
 " t e c h h o u z " do develop reports for our customers from their available data source and new database.
" t e c h h o u z " do develop reports for our customers from their available data source and new database.
 " t e c h h o u z " do assist our customers to manage their valueable data, minimized risk on data lost. We assist in Risk Management and Disaster Recovery, by enable automation of data backup & recovery on (from) premises and cloud.
" t e c h h o u z " do assist our customers to manage their valueable data, minimized risk on data lost. We assist in Risk Management and Disaster Recovery, by enable automation of data backup & recovery on (from) premises and cloud.
 " t e c h h o u z " do design, develop and maintain websites / eCommerce Solutions for any industries, such as restaurants, workshops, shopping malls, hotels, kindergartens, etc.
" t e c h h o u z " do design, develop and maintain websites / eCommerce Solutions for any industries, such as restaurants, workshops, shopping malls, hotels, kindergartens, etc.
 " t e c h h o u z " do assist to setup and host own Private Email Server in Linux and Microsoft Windows.
" t e c h h o u z " do assist to setup and host own Private Email Server in Linux and Microsoft Windows.
 " t e c h h o u z " do assist to setup and own FTP Server in Linux and Microsoft Windows.
" t e c h h o u z " do assist to setup and own FTP Server in Linux and Microsoft Windows.
 " t e c h h o u z " do assist to setup and own Web Server in Linux and Microsoft Windows.
" t e c h h o u z " do assist to setup and own Web Server in Linux and Microsoft Windows.
 Autodesk is the leader in 3D design, engineering and entertainment software. Since its introduction of AutoCAD software in 1982, Autodesk continues to develop the broadest portfolio of 3D software for global markets.
Autodesk is the leader in 3D design, engineering and entertainment software. Since its introduction of AutoCAD software in 1982, Autodesk continues to develop the broadest portfolio of 3D software for global markets.
 Adobe is the global leader in digital marketing and digital media solutions.
Adobe is the global leader in digital marketing and digital media solutions.
 Lumion (Act-3D) was founded in 1998 and officially registered in 2001, dedicated to the development of user-friendly real-time 3D software.
Lumion (Act-3D) was founded in 1998 and officially registered in 2001, dedicated to the development of user-friendly real-time 3D software.
 SketchUp users are architects, designers, builders, makers and engineers. They are the people who shape the physical world. They are important, and they deserve great tools because great tools produce great work.
SketchUp users are architects, designers, builders, makers and engineers. They are the people who shape the physical world. They are important, and they deserve great tools because great tools produce great work.
 GstarCAD is the recognized leading provider of 2D/3D CAD software and solutions for the industries involving AEC, mechanical, manufacturing, electrical, GIS, survey and mapping, civil, etc. With 20 years of proud history of technology innovation and practical application, GstarCAD software is dedicated to providing the fast, powerful and .dwg-compatible CAD software for our customers and partners worldwide.
GstarCAD is the recognized leading provider of 2D/3D CAD software and solutions for the industries involving AEC, mechanical, manufacturing, electrical, GIS, survey and mapping, civil, etc. With 20 years of proud history of technology innovation and practical application, GstarCAD software is dedicated to providing the fast, powerful and .dwg-compatible CAD software for our customers and partners worldwide.
 Microsoft was founded by Paul Allen and Bill Gates on April 4, 1975.
As of 2015, Microsoft is market dominant in both the IBM PC-compatible operating system (while it lost the majority of the overall operating system market to Android) and office software suite markets (the latter with Microsoft Office).
Microsoft was founded by Paul Allen and Bill Gates on April 4, 1975.
As of 2015, Microsoft is market dominant in both the IBM PC-compatible operating system (while it lost the majority of the overall operating system market to Android) and office software suite markets (the latter with Microsoft Office).
 Shinjiru is the largest dedicated web hosting provider in Malaysia. We have been in profitable web hosting business since 1998 with over 40,000 customers. We deliver one server every 6 hours every day. We focus on our core competencies of delivering high quality cloud based web hosting services, provisioning dedicated servers in fast networks with 247 in-house customer support.
Shinjiru is the largest dedicated web hosting provider in Malaysia. We have been in profitable web hosting business since 1998 with over 40,000 customers. We deliver one server every 6 hours every day. We focus on our core competencies of delivering high quality cloud based web hosting services, provisioning dedicated servers in fast networks with 247 in-house customer support.
 we Search, we Analyse, we Provide.
we Search, we Analyse, we Provide.







Please fill up your information as detail as possible so that we can understand you better. We'll revert to you as soon as possible.